Authentication is the process or action of verifying the identity of a user or process. This is in contrast with identification, which is simply the act of indicating a person or thing's identity. Authentication is the process of verifying that identity. As the driving requirement of PSD2, Strong Customer Authentication (SCA) insists on multi-factor — an authentication method in which computer users are granted access only after successfully presenting two or more pieces of evidence (or factors) proving their identity to an authentication mechanism. As shown in the illustration below (click to enlarge), these factors can be:
knowledge – something the user and only the user knows
possession – something the user and only the user has
inherence – something the user and only the user is.
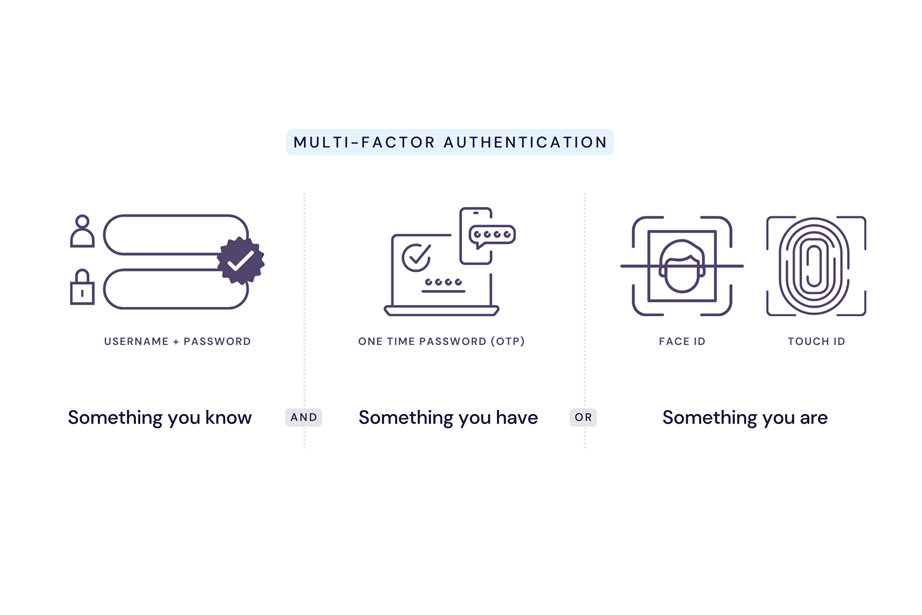
When your customers make a payment with their chip-and-PIN card at the supermarket, they are already using SCA (something they know plus something they have). The idea of SCA in Open Banking is to provide the same or better level of security (for instance, EVM) when users log into their online banking system or a third-party personal finance management app.
In the context of PSD2, SCA applies to “customer-initiated” online payments within Europe. AIS queries and all PIS transfers require SCA.
The following diagram shows the most common models for TPP support of SCA.
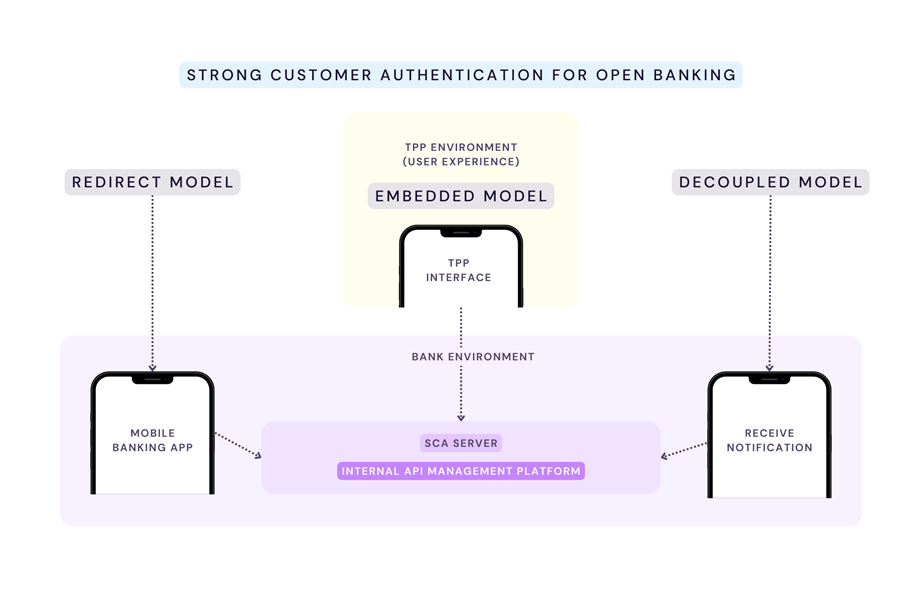
The Token.io platform supports all three SCA models — redirect, decoupled, and embedded. Let's take a brief look at each in turn and the differences encountered.
Under this approach, the PSU connects with the TPP but is redirected to the web ASPSP interface for authentication. Redirection to a mobile app uses the decoupled model.
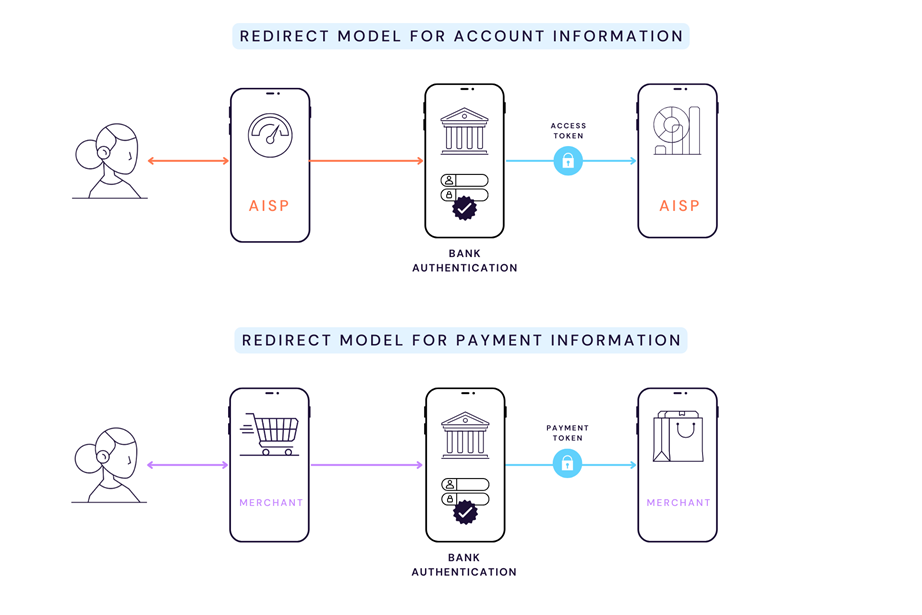
Under the redirect model (pictured above, click to enlarge), the ASPSP manages SCA interactivity with the user; Token.io's Open Banking APIs are not used for SCA operations.
The advantage in the redirect model resides in the Bank/ASPSP remaining in full control of account holder authentication.
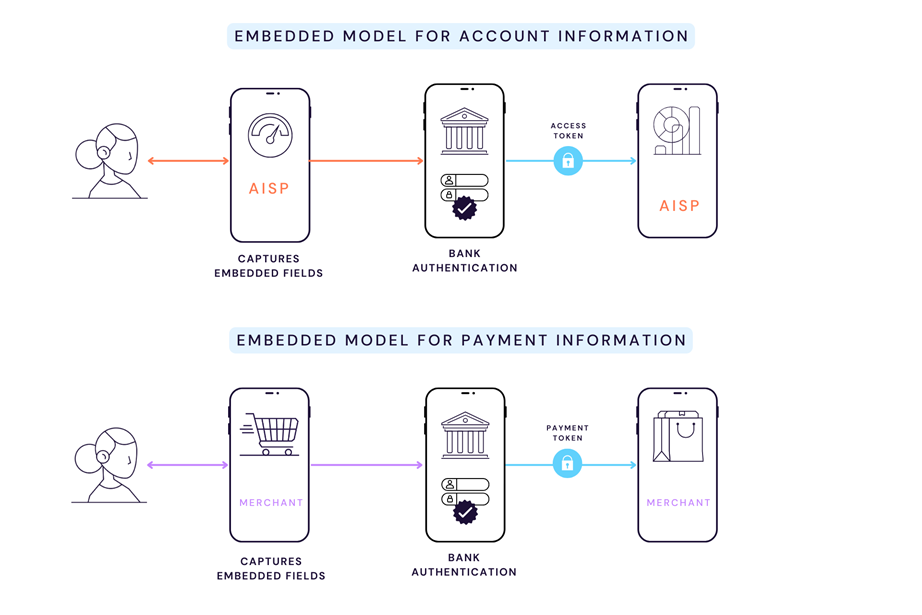
The embedded model is executed entirely through the UI presented by the TPP. User verification is managed locally using a trusted identity provider (IDP) like the device manufacturer (OEM) — wherein user authentication is performed by embedded apps like Apple Pay, Samsung Pay, and Android Pay, among others; typically using biometric verification; i.e., fingerprint scan, iris scan, or FaceID — or through an IDP service like OKTA, which evaluates user authenticity based on the correct entry of a OTP.
Similar to the redirect approach, the decoupled model prompts the PSU to authenticate using the bank's dedicated mobile app on a smartphone or other mobile device, regardless of whether the redirect is launched from a browser or the TPP's mobile app.
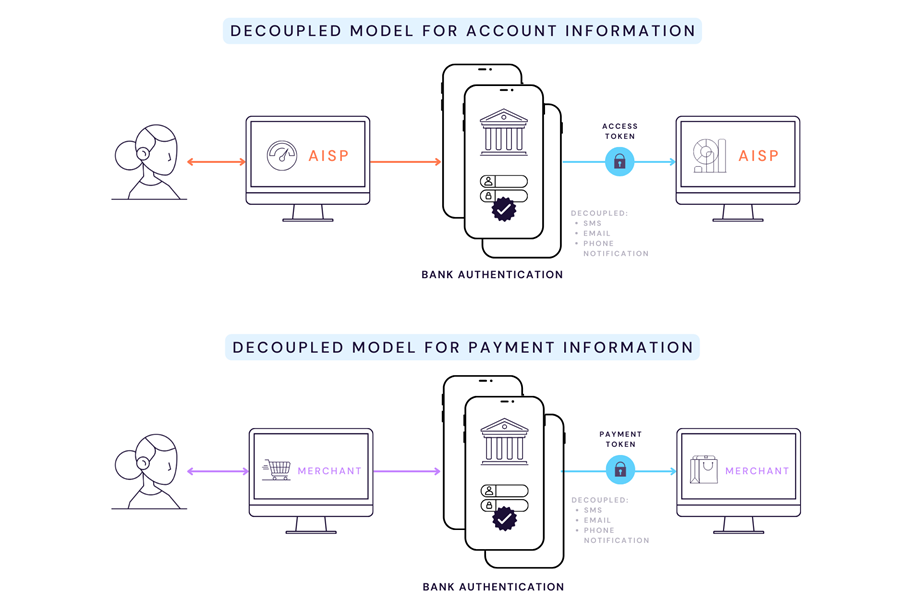
The advantage of bank-controlled SCA remains consistent with the redirect model but a better customer experience for mobile user's is achieved with decoupling.
If you have any feedback about the developer documentation, please contact devdocs@token.io